One Unified Platform
Entitlement reviews should be at the core of cybersecurity, limiting insider access to sensitive systems and data
One platform. One approach. Unprecedented visibility and control.
Delivering improved Risk remediation, Re-certification, Joiner, Mover, Leaver, through cutting edge AI.
idax Risk Manager

A strategic system built for decision-makers and the place to find idax’s unique user experience. This sleek, intuitive interface delivers immediate, high-impact visibility into your organisation’s access risk landscape. With real-time insights and intuitive controls, Risk Manager empowers executives to quickly identify vulnerabilities, drive compliance, and reduce risk exposure—without getting lost in technical complexity.
idax Risk Explorer

Empower every team member to take action on access risk. Risk Explorer makes complex risk data easy to navigate, understand, and remediate—fast. With an intuitive user experience designed for non-technical users, it turns access governance into a shared responsibility.

idax Review & Certify
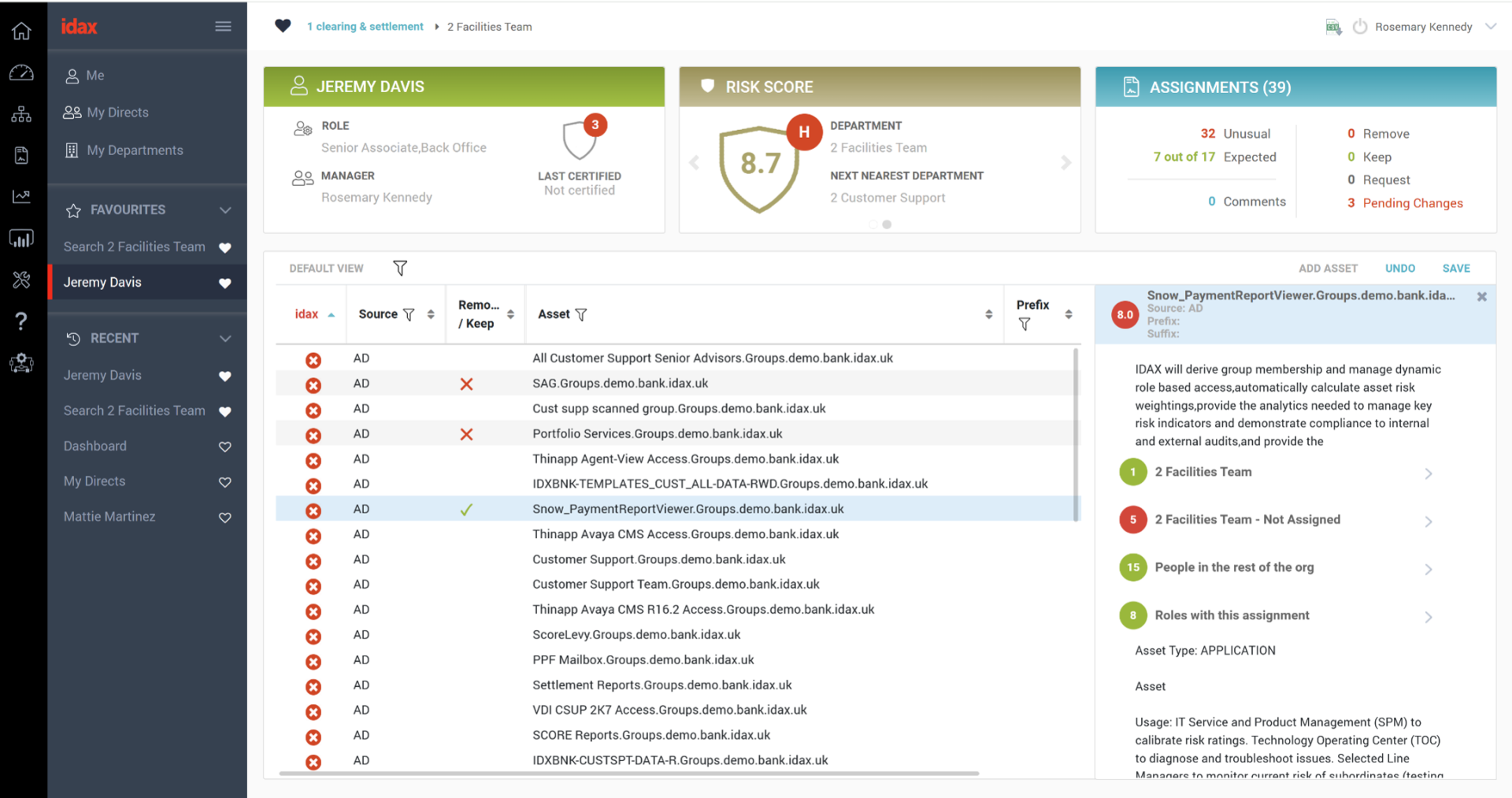
Streamline access reviews and stay audit-ready. This powerful module enables regular, organisation-wide entitlement reviews with built-in automation to remediate risks. Every decision is tracked, giving you a clear,defensible audit trail. Idax certification delivers more comprehensive, measurably better decisions with increased automation for more focused effort.
idax Metrics & Compliance

Turn compliance into a competitive advantage. With real-time reporting via the interface and Power BI integration,you get actionable insights at your fingertips. Proven Key Risk Indicator (KRI) reports track progress and demonstrate to leadership that your access controls are effective and improving.

idax AI Analytics

Unlock the power of Artificial Intelligence with AI that understands your environment. Unlike traditional tools, idax uses advanced algorithms to perform deep risk analysis, uncover hidden access patterns, and automate role and policy design. It puts smart, scalable Role and Attribute Based Access Control within reach—accelerating decisions,reducing manual effort, and continuously improving your security posture.

idax Data Interface

Extend the value of idax across your ecosystem. Our open data interface allows seamless API access and custom data extractions, enabling you to integrate idax’s unique risk intelligence with your existing Identity Access Management (IDAM) platforms and workflows—amplifying insight and control across your environment.
idax Risk Engine
The powerful artificial intelligence engine at the heart of the idax platform. It seamlessly analyses entitlement data, populates the idax database with actionable insights, and delivers results via APIs to the idax user interface and external systems. By identifying users with excessive access, calculating dynamic risk scores, and uncovering hidden patterns in roles and permissions, the Risk Engine gives you unparalleled visibility into access risks—empowering smarter, faster security decisions.